Can we bypass SSL Pinning?
1. What is SSL Pinning and how it works ?
Basically, SSL (Secure Socket Layer) Pinning is a technique that developers use in the client side to avoid man-in-the-middle attack.
Using this technique, developers embed (or pin) a list of trustful certificates to the client application during development, and use them to compare against the server certificates during runtime.
As the client validates the server certificates again even after SSL handshaking, if there is a mismatch between the server and the local copy of certificates, the connection will simply be disrupted, and no further user data will be even sent to that server.
2. Difference between with and without SSL Pinning ?
This enforcement ensures that the user devices are communicating only to the trustful servers.
Thus, it is often used to prevent man-in-the-middle apps which generate its own self-signed certificate, from analyzing the functionality of the app and the way it communicates with the server.
To illustrate, let’s try capturing Product Hunt and Dropbox‘s traffics with Proxyman.
As you can see, Product Hunt does not use SSL Pinning for its client. Thus, Proxyman can act as both server/client to communicate and capture all transmitted data coming from and to Product Hunt
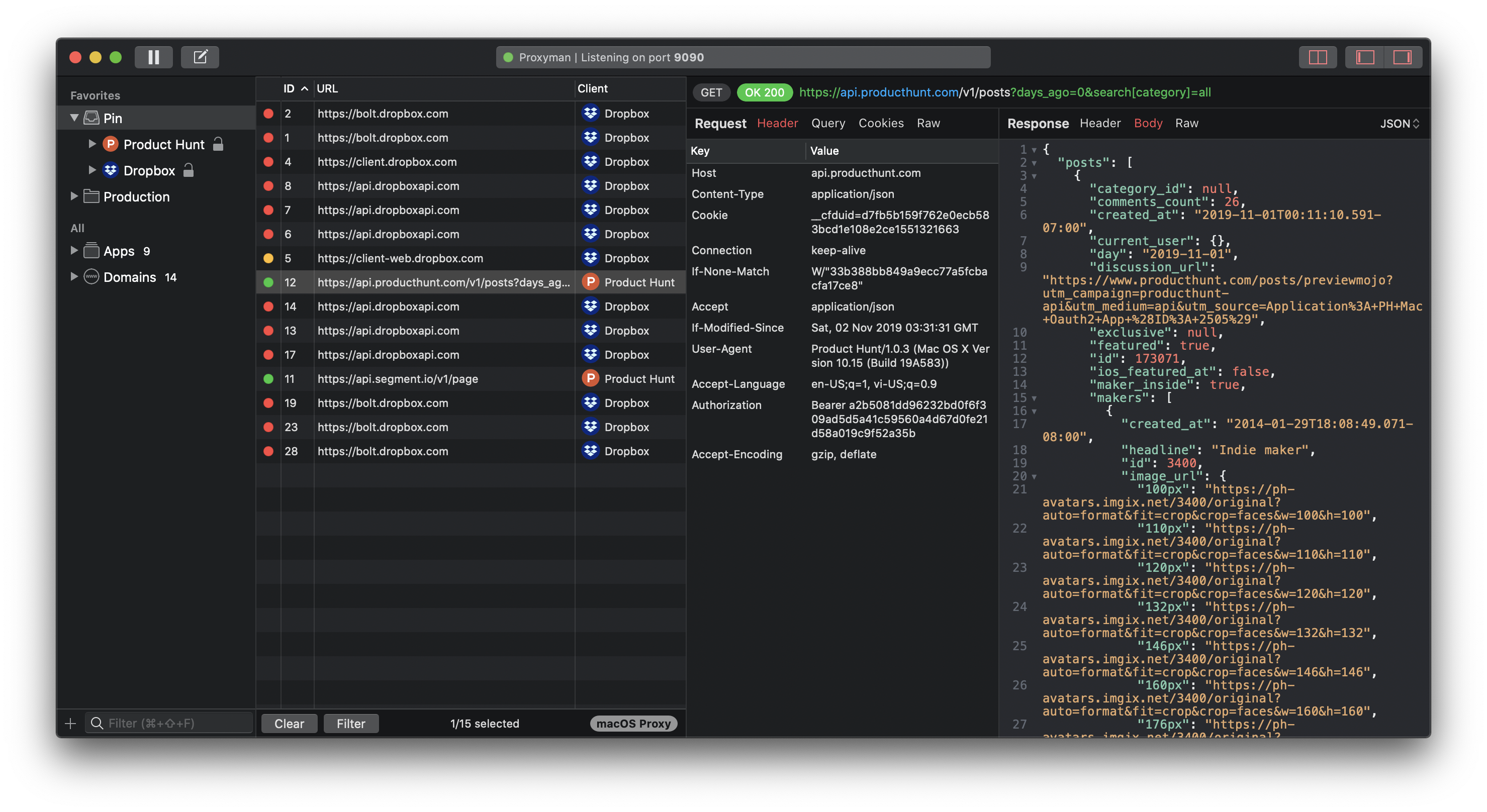
Product Hunt traffics are captured by Proxyman
Meanwhile, with SSL Pinning, all requests to server are disconnected as Dropbox client detects Proxyman CA is not in the predefined certificate list.
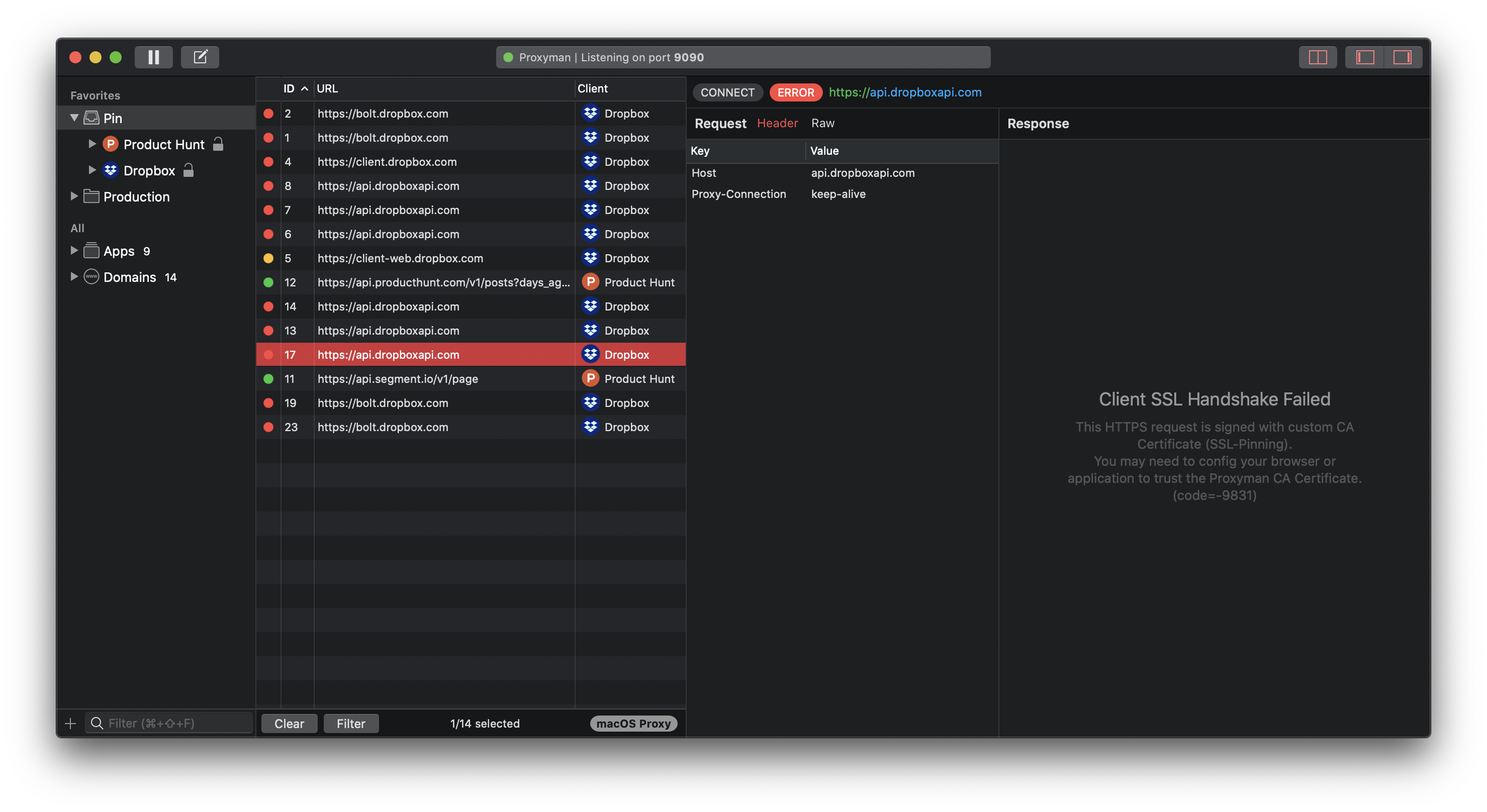
Dropbox traffics are not captured by Proxyman
3. Can we bypass SSL Pinning?
Now we know that restricting the set of trusted certificates through pinning could prevent attackers, but is there anyway to bypass this protocol? The answer is both Yes and No (:
-
If we are not developers of the company, chances are we are unable to provide the valid certificate to communicate with the app’s client.
-
However, if we are developers of the company, who does have the original certificate and the associated private key, we can add those keys to a man-in-the-middle app to bypass SSL Pinning.
With that being said, not all of man-in-the-middle applications support adding keys to bypass this protocol (:
4. Where to go from here ?
This mini blog just gives a basic understanding of why sometimes developers can not inspect traffics coming from/to an app.
For further information of how SSL Pinning works and how to implement this protocol on your app, you might visit the RWL course here.
You could also use Proxyman that acts as man-in-the-middle app to test SSL Pinning on your app (:
Proxyman is a high-performance macOS app, which enables developers to view HTTP/HTTPS requests from apps and domains on iOS device, iOS Simulator and Android devices.
Get it at https://proxyman.com

